The certifications Human-I-T possesses ensures that our data destruction professionals collect, handle, transport, and and destroy your information while adhering to a strict chain of custody procedure, and that your data will be destroyed according to state and federal regulations that apply to your business.
Certified Secure Data Destruction
Get Your Questions Answered About Our Data Destruction PracticesOur Certifications Ensure Your Peace of Mind
Technology Partners





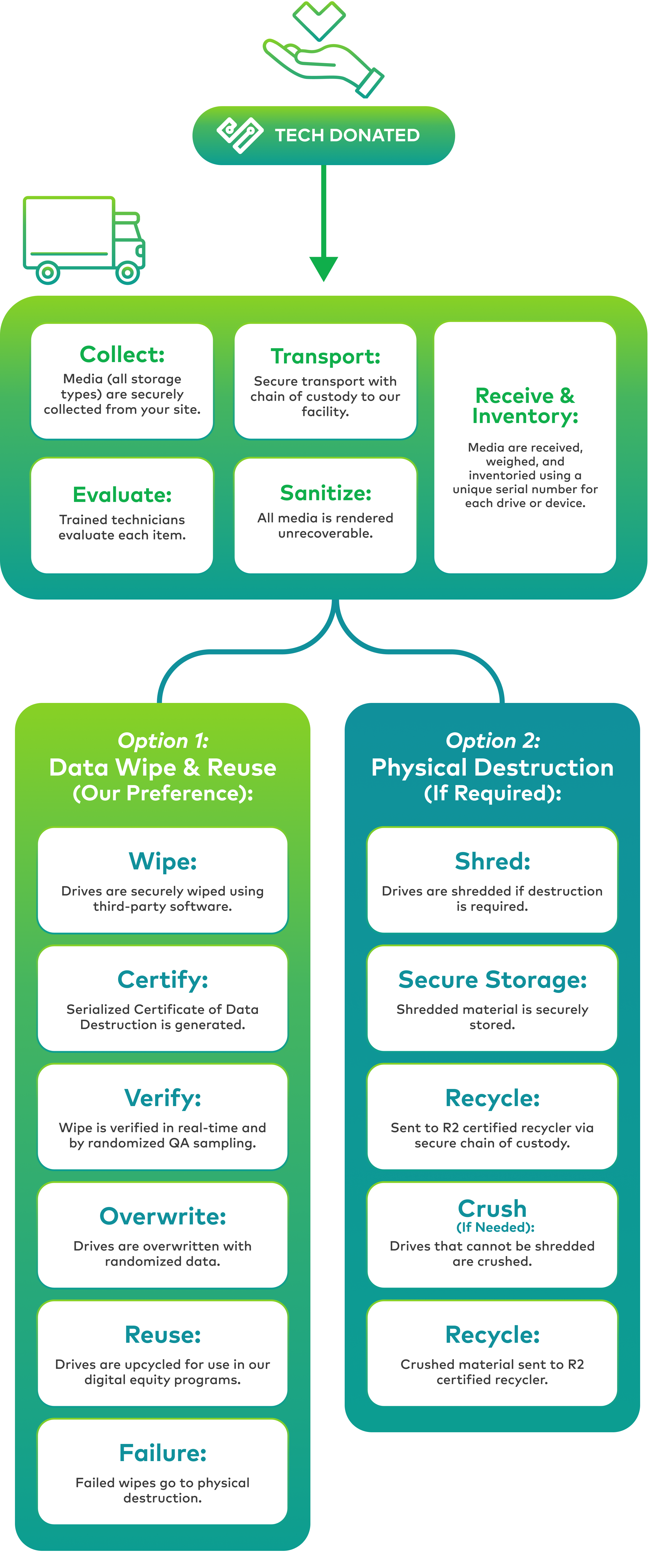
How We Keep Your Data Secure
Secure Transportation & Storage
All devices with data storage will be received by authorized Human-I-T personnel at a NAID-certified, secure facility where they will be physically secured and closely supervised until processed.
Comprehensive Data Sanitization
Using a NIST 800-88 method, random data is written through the entirety of the device with data storage in order to destroy all recoverable data on the device. The device with data storage is then re-scanned to verify that 100% of all sensitive information has been destroyed.
Physical Destruction
If we cannot erase all sensitive data using our software, the device with data storage will be physically destroyed and recycled in an environmentally sound manner, via an R2-certified organization.

Providing you assurance with comprehensive verification
We take extra steps so you don’t have to. Because we understand that with all your other difficult job responsibilities, direct oversight of tech disposal shouldn’t have to be one of them.

Certifies that all items which have been appropriately accounted for have been destroyed

A serialized PDF report of all devices with data storage that had their data sanitized to show you things like the items’ serial numbers, their Human-I-T donation IDs, and the date they were each received

Similar to the Data Destruction Report, this report provides all the information you’ll want about the devices that were physically destroyed, including serial number, destruction method, and technician name.
The Chain of Custody
An easy, no-hassle experience from start to finish

Human-I-T Secure Pickups
Your donations are transported securely in either Human-I-T’s GPS-tracked trucks with four cameras, or by one of our partners. Either way, the safety of your tech is guaranteed. You can also access Human-I-T truck live feeds and up to two months of recorded footage for complete peace of mind.

Shipped Donations
Enjoy the assurance of real-time tracking for all shipped donations, whether by parcel or freight, keeping you informed every step of the way.

Prepaid Laptop Boxes
For laptop-only donations, we offer secure, padded laptop boxes, making it convenient and safe to send your items to us.

Facility Security
Our facility is NAID- and ISO-certified, featuring advanced ADT security and rigorous background checks for all staff, ensuring the highest level of protection for your donated items.
What sets our services apart?
Have questions?
Ready to get rid of your tech?
Fill out the form below to speak directly with a member of our team!
What our certifications mean for you:
NAID AAA
NAID AAA means that a company has been verified by the National Association of Information Destruction (NAID) to meet strict standards for information destruction. NAID certification is a voluntary program administered by i-SIGMA that verifies secure information destruction practices through rigorous scheduled and unannounced audits, helping organizations protect sensitive data and avoid security breaches, fraud, and compliance penalties.
ISO 90001
ISO 9001 is an international standard that defines the requirements for implementing and maintaining a quality management system (QMS), helping organizations improve their performance and meet customer expectations.
ISO 14001
ISO 14001 is a set of standards that helps organizations reduce their environmental impact by establishing an effective environmental management system (EMS).
ISO 45001
ISO 45001 is the international standard for occupational health and safety management systems that helps organizations improve workplace safety and reduce risks. Organizations use it to demonstrate legal compliance, reduce incidents and absenteeism, while improving productivity, insurance costs, and employee morale.
M360
M360 is a mobile diagnostics and utility software that is certified by ADISA as a reliable software for data erasure. This certification ensures that M360 can securely and permanently erase data.
We are compliant with the following laws:
HIPAA
Data Security for Health Plans, Health Care Clearinghouses, and Health Care Providers
HIPAA, the Health Insurance Portability and Accountability Act, sets the standard for protecting sensitive patient data. Any company that deals with protected health information (PHI) must ensure that all the required physical, network, and process security measures are in place and followed.
Workstation and Device Security. A covered entity must implement policies and procedures to specify proper use of and access to workstations and electronic media. A covered entity also must have in place policies and procedures regarding the transfer, removal, disposal, and re-use of electronic media, to ensure appropriate protection of electronic protected health information (e-PHI).
GLBA
Data Security for Banks and Financial Institutions
The Gramm-Leach-Bliley Act requires financial institutions – companies that offer consumers financial products or services like loans, financial or investment advice, or insurance – to explain their information-sharing practices to their customers and to safeguard sensitive data. Specifically, human-I-T helps assist Banks, Credit Unions and other companies adhere to the Federal Trade Commission’s (FTC’s) Disposal Rule. Where applicable, the GLBA requires that customer information is disposed of in a secure way.
FACTA
Data Security for Credit Institutions and Reporting Agencies
The Fair and Accurate Credit Transaction Act of 2003 (FACTA) added sections to the federal Fair Credit Reporting Act (FCRA, 15 U.S.C. 1681 et seq.), intended primarily to help consumers fight the growing crime of identity theft. Accuracy, privacy, limits on information sharing, and new consumer rights to disclosure are included in FACTA.
FISMA
Data Security for Federal Executive Branch Civilian Agencies
FISMA requires federal agencies to implement a mandatory set of processes and system controls designed to ensure the confidentiality, integrity, and availability of system-related information. The processes and systems controls in each federal agency must follow established Federal Information Processing Standards, National Institute of Standards and Technology standards, and other legislative requirements pertaining to federal information systems, such as the Privacy Act of 1974.
PIPEDA
Data SEcurity for Private SEctor Organizations and Commercial Activity
The Personal Information Protection and Electronic Documents Act (PIPEDA) sets out ground rules for how private sector organizations may collect, use or disclose personal information in the course of commercial activities. PIPEDA also applies to federal works, undertakings and businesses in respect to employee personal information. The law gives individuals the right to access and request correction of the personal information these organizations may have collected about them.
SOX
Data Security for Public Companies and Financial Reporting
The Sarbanes-Oxley Act of 2002 (SOX) mandated a number of reforms to enhance corporate responsibility, enhance financial disclosures and combat corporate and accounting fraud. It created the “Public Company Accounting Oversight Board,” also known as the PCAOB, to oversee the activities of the auditing profession.
FAQs
What is the Human-I-T data sanitization process?
We sanitize all devices with data storage at our NAID-certified facilities using DoD and HIPAA-compliant NIST 800-88 software. In the event not all data can be destroyed, we crush the storage and then responsibly dispose of the physical assets through an R2-certified organization.
What data security certifications does Human-I-T have?
We are NAID AAA Certified. More specifically, this certification recognizes that our facilities passed rigorous, unannounced audits by the National Association of Information Destruction to ensure every element of our data security and destruction practices.
What type of data destruction reporting does Human-I-T provide?
Every donation comes with a general Certificate of Data Destruction. For an added layer of data security reporting, we can also offer a Data Sanitization Wipe Report or Physical Crushing Report. Please connect with your Human-I-T representative to discuss our reporting options further!
Ready to start making an impact with your technology or have more questions?
Please provide your information here and a Human-I-T representative will be in touch in 1 business day.


